CMMC Overview
The Cybersecurity Maturity Model Certification (CMMC) is a major Department of Defense (DoD) program built to protect the defense industrial base (DIB) from increasingly frequent and complex cyber-attacks. It particularly aims to enhance the protection of controlled unclassified information (CUI) and federal contract information (FCI) shared within the DIB.
CMMC builds on existing trust-based regulations (DFARS 252.204-7012) by adding a verification component for cybersecurity requirements. CMMC is closely aligned with NIST 800-171.
DoD's Office of the Under Secretary of Defense for Acquisition & Sustainment [OUSD(A&S)] developed the CMMC Framework, working with DoD stakeholders, University Affiliated Research Centers (UARCs), Federally Funded Research and Development Centers (FFRDC), and industry. The Framework combines various cybersecurity standards and best practices intended to:
- Safeguard sensitive information to enable and protect the warfighter
- Dynamically enhance DIB cybersecurity to meet evolving threats
- Ensure accountability while minimizing barriers to compliance with DoD requirements
- Contribute towards instilling a collaborative culture of cybersecurity and cyber resilience
- Maintain public trust through high professional and ethical standards
Cybersecurity is a top priority for the Department of Defense.
The Defense Industrial Base (DIB) is the target of more frequent and complex cyberattacks. To protect American ingenuity and national security information, the DoD developed the Cybersecurity Maturity Model Certification (CMMC) 2.0 program to reinforce the importance of DIB cybersecurity for safeguarding the information that supports and enables our warfighters.
Who is subject to CMMC?
All DoD prime- and sub-contractors planning to bid on future contracts with the CMMC DFARS clause will be required to obtain a CMMC certification prior to contract award. Some prime- and sub-contractors accessing, processing or storing FCI (but not CUI) will minimally require a Level 1 attestation. A DoD contract will specify which level of compliance a contractor needs to meet.
All DIB members should learn the CMMC's technical requirements not only for certification but for long-term cybersecurity agility. However, DoD recognizes that many DIB members are small businesses that lack the resources of their larger, prime counterparts. As a result, the CMMC Framework incorporates cost-effective and affordable controls for small businesses to implement at the lower CMMC levels.
Overall, CMMC is designed to provide DoD increased assurance that a DIB company can adequately protect sensitive CUI and FCI, accounting for information flow down to subcontractors in a multi-tier supply chain.
Overview of the CMMC Program
The Cybersecurity Maturity Model Certification (CMMC) program is aligned to DoD’s information security requirements for DIB partners. It is designed to enforce protection of sensitive unclassified information that is shared by the Department with its contractors and subcontractors. The program provides the Department increased assurance that contractors and subcontractors are meeting the cybersecurity requirements that apply to acquisition programs and systems that process controlled unclassified information.
The CMMC 2.0 program has three key features:
- Tiered Model: CMMC requires that companies entrusted with national security information implement cybersecurity standards at progressively advanced levels, depending on the type and sensitivity of the information. The program also sets forward the process for requiring protection of information that is flowed down to subcontractors
- Assessment Requirement: CMMC assessments allow the Department to verify the implementation of clear cybersecurity standards.
- Implementation through Contracts: Once CMMC is fully implemented, certain DoD contractors that handle sensitive unclassified DoD information will be required to achieve a particular CMMC level as a condition of contract award.
CMMC Maturity Levels
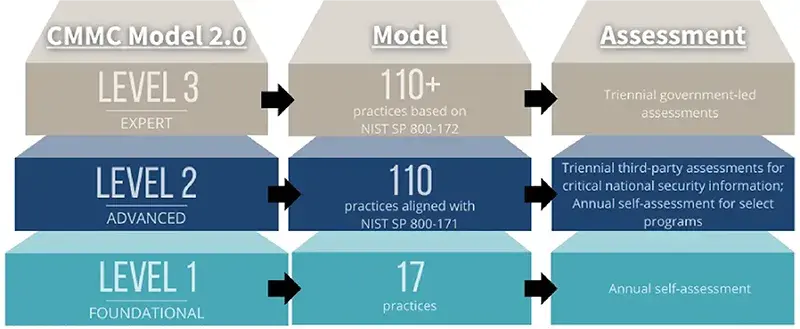
The CMMC Framework requires a systematic approach to certification mapped to three organizational maturity levels: Foundational, Advanced, and Expert.
- Level 1 - Foundational. An organization must demonstrate basic cyber hygiene practices, such as ensuring employees change passwords regularly to protect Federal Contract Information (FCI). FCI is "information, not intended for public release, that is provided by or generated for the Government under a contract to develop or deliver a product or service to the Government."
- Level 2 - Advanced. An organization must have an institutionalized management plan to implement good cyber hygiene practices to safeguard CUI, including all the NIST 800-171 r2 security requirements and processes
- Level 3 - Expert. An organization must have standardized and optimized processes in place and additional enhanced practices that detect and respond to changing tactics, techniques and procedures (TTPs) of advanced persistent threats (APTs). An APT is as an adversary that possesses sophisticated levels of cyber expertise and significant resources to conduct attacks from multiple vectors. Capabilities include having resources to monitor, scan, and process data forensics.
CMMC Framework Levels
The CMMC framework, which links the model to a systematic approach to achieve certification level, consists of several assets: domains (14), and practices (110+) corresponding to the certification level.
- Level 1 (Performed: 17 practices). An organization must demonstrate basic cyber hygiene practices, such as ensuring employees change passwords regularly to protect Federal Contract Information (FCI). FCI is "information, not intended for public release, that is provided by or generated for the Government under a contract to develop or deliver a product or service to the Government."
- Level 2 (Managed: 110 practices). An organization must have an institutionalized management plan to implement good cyber hygiene practices to safeguard CUI, including all the NIST 800-171 r2 security requirements and processes.
- Level 3 (Optimizing: 110+ practices). An organization must have standardized and optimized processes in place and additional enhanced practices that detect and respond to changing tactics, techniques and procedures (TTPs) of advanced persistent threats (APTs). An APT is as an adversary that possesses sophisticated levels of cyber expertise and significant resources to conduct attacks from multiple vectors. Capabilities include having resources to monitor, scan, and process data forensics.
To achieve certification at each level, organizations undergo a third-party assessment by an accredited and certified CMMC assessor who evaluates their adherence to the required practices and processes. The certification demonstrates the organization's commitment to cybersecurity and its ability to protect sensitive information within the defense supply chain.
It is important to note that the specific set of practices and processes required at each level are outlined in the CMMC model documentation, and organizations must align their cybersecurity programs accordingly to achieve the desired certification level. CMMC Governance
The CMMC governance process refers to the framework and procedures established to oversee and manage the implementation, assessment, and certification of the Cybersecurity Maturity Model Certification (CMMC) within an organization. It involves various steps and activities to ensure compliance with CMMC requirements and maintain the security of sensitive information. While the specific governance process may vary depending on the organization, here are some common elements:
- Establishing Policies and Procedures: The governance process begins with defining and documenting policies, procedures, and guidelines related to cybersecurity and CMMC compliance. This includes developing a cybersecurity policy, incident response plan, access control procedures, and other relevant documentation.
- Assigning Responsibility: Clearly defining roles and responsibilities within the organization is crucial for effective CMMC governance. Designate individuals or teams responsible for overseeing cybersecurity efforts, managing CMMC compliance, and coordinating assessments and certifications.
- Training and Awareness: Conduct regular cybersecurity training and awareness programs for employees to ensure they understand their roles, responsibilities, and the importance of adhering to CMMC requirements. This includes educating employees on cybersecurity best practices, incident reporting procedures, and the organization's policies and procedures.
- Implementing Controls and Practices: Implement the necessary cybersecurity controls and practices based on the specific CMMC level the organization is aiming to achieve. This includes deploying technical solutions, establishing access controls, conducting vulnerability assessments, and enforcing security policies.
- Conducting Self-Assessments: Perform regular self-assessments to evaluate the organization's compliance with CMMC requirements. Self-assessments can help identify any gaps or weaknesses and allow for corrective actions to be taken before the formal assessment.
- Engaging with Third-Party Assessors: When the organization is ready, engage with certified Third-Party Assessment Organizations (C3PAOs) to undergo an official CMMC assessment. The C3PAO will evaluate the organization's cybersecurity practices and determine if it meets the requirements for the desired CMMC level.
- Remediation and Continuous Improvement: If any deficiencies or non-compliance issues are identified during the assessment, develop and implement remediation plans to address them. Additionally, establish a process for continuous improvement by regularly reviewing and updating cybersecurity controls, practices, and policies based on emerging threats and industry best practices.
- Maintaining Documentation: Maintain proper documentation of policies, procedures, assessments, certifications, and other relevant records to demonstrate compliance with CMMC requirements. This documentation is necessary for ongoing governance, audits, and future assessments.
The governance process ensures that the organization maintains a robust cybersecurity posture, aligns with CMMC requirements, and continuously improves its cybersecurity practices to protect sensitive information and support the defense supply chain.
The Evolution to CMMC 2.0
In September 2020, the DoD published an interim rule to the DFARS in the Federal Register (DFARS Case 2019-D041), which implemented the DoD’s initial vision for the CMMC program (“CMMC 1.0”) and outlined the basic features of the framework (tiered model, required assessments, and implementation through contracts). The interim rule became effective on November 30, 2020, establishing a five-year phase-in period.
In March 2021, the Department initiated an internal review of CMMC’s implementation, informed by more than 850 public comments in response to the interim DFARS rule. This comprehensive, programmatic assessment engaged cybersecurity and acquisition leaders within DoD to refine policy and program implementation.
In November 2021, the Department announced “CMMC 2.0,” an updated program structure and requirements designed to achieve the primary goals of the internal review:
- Safeguard sensitive information to enable and protect the warfighter
- Enforce DIB cybersecurity standards to meet evolving threats
- Ensure accountability while minimizing barriers to compliance with DoD requirements
- Perpetuate a collaborative culture of cybersecurity and cyber resilience
- Maintain public trust through high professional and ethical standards
Key Features of CMMC 2.0
*** Comparison between CMMC Models 1.0 and the planned CMMC Model 2.0. The CMMC Model 2.0 is notional until rulemaking is completed. ***
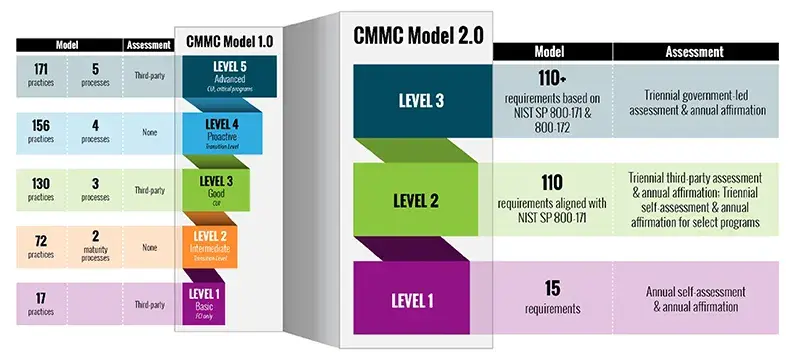
With the implementation of the Cybersecurity Maturity Model Certification (CMMC) 2.0 program, the Department is introducing several key changes that build on and refine the original program requirements. These are:

Streamlined Model
- Focused on the most critical requirements: Streamlines the model from 5 to 3 compliance levels
- Aligned with widely accepted standards: Uses National Institute of Standards and Technology (NIST) cybersecurity standards

Reliable Assessments
- Reduced assessment costs: Allows all companies at Level 1, and a subset of companies at Level 2, to demonstrate compliance through self-assessments
- Higher accountability: Increases oversight of professional and ethical standards of third-party assessors

Flexible Implementation
- Spirit of collaboration: Allows companies, under certain limited circumstances, to make Plans of Action & Milestones (POA&Ms) to achieve certification
- Added flexibility and speed: Allows the Government to waive inclusion of CMMC requirements under certain limited circumstances
Rulemaking and Timeline for CMMC 2.0
The changes reflected in CMMC 2.0 will be implemented through the rulemaking process. Companies will be required to comply once the forthcoming rules go into effect. The Department intends to pursue rulemaking both in Part 32 of the Code of Federal Regulations (C.F.R.) as well as in the Defense Federal Acquisition Regulation Supplement (DFARS) in Part 48 of the C.F.R. Both rules will have a public comment period. Stakeholder input is critical to meeting the objectives of the CMMC program, and the Department will actively seek opportunities to engage stakeholders as it drives towards full implementation.
While these rulemaking efforts are ongoing, the Department has suspended prior CMMC Piloting efforts.
The Department encourages contractors to continue to enhance their cybersecurity posture during the interim period while the rulemaking is underway. The Department has developed Project Spectrum to help DIB companies assess their cyber readiness and begin adopting sound cybersecurity practices.